The ssh debug says: debug1: Connection to port 7000 forwarding to localhost port 7000 requested. Debug1: channel 2: new direct-tcpip channel 2: open failed: connect failed: Connection refused debug1: channel 2: free: direct-tcpip: listening port 7000 for localhost port 7000, connect from 127.0.0.1 port 53954, nchannels 3. The OpenSSH SSH client supports SSH protocols 1 and 2. Protocol 2 is the default, with ssh falling back to protocol 1 if it detects protocol 2 is unsupported. These settings may be altered using the Protocol option in sshconfig(5), or enforced using the -1 and -2 options (see above). May 18, 2020 Enter your local port number in the Source port field. Type the destination address and port number in the Destination field. Use the following format. Once you verify that the information you entered is correct, select Add. The parameters for the connection are now all set. The Open option.
Let’s imagine for a second that your IT manager leaves you in charge of installing a next-generation firewall to filter incoming and outgoing traffic—but you don’t fully understand how open ports work, why they’re open, and which ones you need to filter.
A network firewall is a great mitigation tool, but it won’t help you configure the filtering rules completely (some do, but they don’t always suggest the most accurate and secure configuration), nor will it enlighten you to all the security needs of the system services that are running.
Open Ssh Port Ubuntu 20.04
When you read through technical blogs, manuals and other resources regarding port scanning and open ports, you’re likely to get many suggestions about closing your open ports. But where are those suggestions coming from? Is it really necessary to close all the open ports? Are all open ports sign of active vulnerabilities?
Let’s find out.
What is an open port?
Open Ssh Port Centos 7
Whenever we say “port” it could be related to two concepts: the hole located at the back or side of any network device, such as an ethernet port, or, when it’s related to IP addresses and Internet-based services, we’re talking about virtual ports that can be “open” (used) or “closed” (free).
Internet servers include many running services; for example, an HTTP server that lets you browse the securitytrails.com page, or an email server that enables people to send and receive email. On the other side of things, developers use file transfer protocols such as the FTPS or the classic SSH to run encrypted tunnels across computers that are used to share information between hosts.
And this is where the ‘port’ concept comes in. A port is basically a way to help systems identify, establish and transmit data from one side to the other.
Ports are designated by numbers. For instance, if a port is open (used) it can be listening on any number in the 1-65535 range. That’s right, there are 65,535 possible ports that could be assigned to any services.
And when you install an operating system on your desktop PC or on any virtual machine—and you install, say, Nginx or Exim—a port will be needed in order to have that daemon (service) ready to receive and send data over the network.
Once a port is running on a certain number, you can’t run other services on that same port. For example, starting Apache after you’ve already started Nginx on port 80 will lead to a failed operation because the port is already in use.

Know that whenever you browse a page, you’re connecting to port 80 (for HTTP) or 443 (for HTTPS based requests), or whenever you request information from a remote SSH server you’ll probably do it through port 22.
As you can see, open ports help network devices and operating systems communicate with each other and transmit the correct information in the appropriate way.
Closed ports, on the other hand, are merely ports that no longer have any services listening on them. If you perform ‘service nginx stop’, you’ll be closing all the established connections, and none will be able to reach your website until you ‘start’ (open) it again.
Are open ports dangerous?
There’s a common misconception that open ports are dangerous. A lot of IT media suggests that you “close ports,” and while this may be appropriate in some scenarios, it’s not accurate to say that open ports are dangerous.
When we really think about it, we recognize that open ports have been there since the beginning of the Internet. After all, open ports are the ones that help you communicate with your colleagues, friends and family over the entire network services stack.
So instead of saying flat-out that open ports are dangerous, we could simply say that misconfigured server and network security rules, along with unpatched and vulnerable software, are what ultimately lead companies to service exploitation… and only on certain ports.
This is because open ports aren’t dangerous by default. It’s what we do with open ports at system level, and what we expose on the services and apps running on those ports, that prompts people to label them as “dangerous” or not.
What are the common open ports?
There are a lot of port scanners around, some built for that specific task, and others included in vulnerability scanning online tools. No matter how you use them, know that port scanning is a must for discovering open ports.
But what are the most popular open ports these days? Take a look below. This is by no means a definitive list, but a brief run-down of popular ports found in many online-connected machines.
- FTP - 20, 21 are the ports used during a classic FTP connection between client and server.
- SSH - 22 is the OpenSSH server port used by default on most Unix/Linux installations.
- Telnet - 23 is dedicated to the Telnet application server that receives connections from any Telnet client.
- SMTP - 25 is dedicated to relaying messages between MTAs (mail transfer agents).
- DNS - 53 is where the DNS server runs, and one of the most famous daemons that uses this port is Bind.
- DHCP - 67, 68: port 67 is used for the DHCP server, and the UDP port 68 for the DHCP client.
- HTTP - 80 is the port assigned to web servers and directly associated with the Hypertext Transfer Protocol.
- POP3 - 110 is the Post Office Protocol, one of the most traditional protocols used by email clients to retrieve data from remote email servers.
- IMAP - 143 is the default IMAP port for non-encrypted connections.
- HTTPS - 443 is the port used to serve all SSL-based requests on any website.
What are the default open ports?
Open Ssh Port Ubuntu
This depends entirely on the operating system you’re running, as not all OSs run the same services. For example, Windows, MacOS and Linux all run different core daemons, therefore, a port that is open on one could be closed on the other.

On our top scanned ports blog post, we analyzed the most scanned ports. That data could lead to an answer for this question, but not necessarily when it comes to default open ports.
The list of default open ports could be huge depending on the OS, version or distribution. For example, MacOS websites state that there are around 132 ports that could potentially be used on many of their Apple services.
On others, the list of default open ports could be reduced to none.
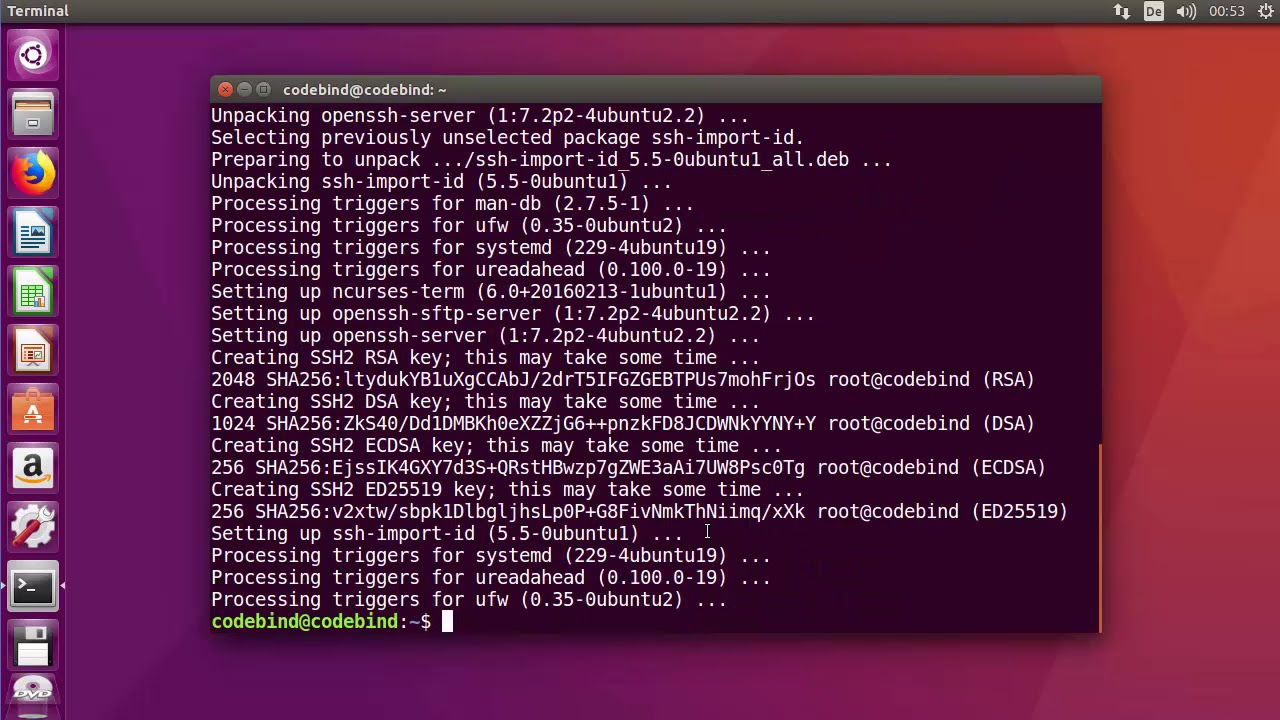
In our testing, running a full Nmap scan on an Ubuntu image leads us to discover these ports open by default:
As you can see, by default all Ubuntu 18.x DigitalOCean images used to create droplets have SSH enabled by default running on port 22—which is logical, because otherwise you wouldn’t have a way to connect to the server.
CentOS, on the other hand, had three open ports by default, as shown in the following screenshot:
How do I find out what ports are open on my online infrastructure?
The first answer to basic port scanning stuff is always Nmap.
In order to scan a local machine you can do it by issuing the following command:
nmap -p 1-65535 localhost
If you want to run a scan against any other remote network, you can do it by using:
nmap -p 1-1024 X.X.X.X
(Where “X.X.X.X” is the remote IP address you want to target.)
From 1 to 65535, you can scan any range you need, just keep in mind that larger ranges will take more time.
If you want to scan the most popular ports, you can do it by using this syntax:
nmap --top-ports 20 X.X.X.X
Firewalld Open Ssh Port
(Where “20” is the number of popular ports you want to target.)
Output example:
However, Nmap is a terminal-based tool, so it’s only useful for real geeks!

Open Ssh Port On Windows
If you want to switch to a web-based tool that works for both terminal gurus and average IT users, you may be interested in discovering real power in the port scanning features of SurfaceBrowser™.
SurfaceBrowser™ is one of the most complete infosec utilities available when it comes to generating a full OSINT summary about all your internet-based assets. It will help you discover how much information you’re exposing on both the Internet surface and in shadow data, behind the scenes.
Our OSINT tool will give you all the open port data instantly, with no waiting or manual scans needed. It’s all there.
Let’s explore how easy it is to detect which open ports are available for any given domain name. In this example, we’ll check out all the available open ports for the linode.com domain name.
As you can see, we found a lot of interesting information—including 9 open ports across all their *.linode.com hosts:
- 22 - Secure Shell (SSH)
- 80 - Hypertext Transfer Protocol (HTTP)
- 443 - Hypertext Transfer Protocol over TLS/SSL (HTTPS)
- 21 - FTP
- 6379 - Redis
- 11211 - memcached
- 9200 - WSP
- 5984 - CouchDB database server
- 990 - FTPS Protocol
There are a lot of open ports here, including critical services such as SSH, Memcached, FTP and others.
Open ports found on subdomains
One of the top activities performed by security researchers and penetration testers is DNS enumeration. This is often used to find subdomains and create a digital map of all your online infrastructure.
Then, they usually scan ports, wait for the results, and cross all the mapping and port scanning data, losing a lot of time during investigations and tests.
SurfaceBrowser™ enables you to access the full DNS map of any domain name including all the subdomains, as well as the exact number of open ports on each host and a summary that lets you quickly pivot between all the information:
Open Ssh Port
Using the ‘Summary by Open Ports’ widget will save you valuable time in finding critical information about your own infrastructure, or when you’re investigating a 3rd party company.
Summary
Ports are always one of the first doors knocked on by attackers. If found open, they can become a real threat if the services you’re running on them aren’t properly hardened from a network, operating system and app point of view.
If you work for a web-based company, staying on top of your open ports before the bad guys get to them is one of your first priorities. This gives you a great head start on reviewing, hardening and closing unneeded ports to reduce your attack surface area.
Don’t lose any more time. Get full access to the most effective port scanner and DNS mapping tool ever: explore SurfaceBrowser™ or book a demo with our sales team today!
Open Ssh Port Kali
Esteban is a seasoned security researcher and cybersecurity specialist with over 15 years of experience. Since joining SecurityTrails in 2017 he’s been our go-to for technical server security and source intelligence info.
Get the best cybersec research, news, tools,
and interviews with industry leaders
